
This is an old school LG G3 that was sent in completely dead. The screws on the back of the phone show significant rust indicating that it was dropped into water at some point. Definitely explains why it won’t turn on!

I have gone ahead and removed the motherboard from the phone. I will be using the chip off method to access the data and recover the wallet.

On the back of the motherboard is the EMMC chip where all the data is stored. It’s encased in a special black potting epoxy all around it to protect it. The epoxy has to be removed first before the chip can be desoldered from the motherboard, so here I have begun to scrape away at it from the sides.

To remove the potting epoxy and desolder the EMMC chip so it can be read from I have a setup with a microscope, hot air soldering station, and other assorted soldering irons.

The EMMC chip has been desoldered from the motherboard now. Here you can see a better view of the black potting epoxy that has been used to encase the chip. The silver pads beneath where the chip used to go are the pads on the motherboard that connect to the chip.

I put the chip into a vise so I can begin cleaning it up and removing any left over potting epoxy and solder. Unfortunately I didn’t get any photos of this stage but it was pretty messy anyways.

Here it is all cleaned up and ready for reading. You can see it is barely the size of a dime!

The EMMC chip then goes into this EMMC reader to read the data directly from the EMMC chip.

Now we can plug the reader into the computer and begin exploring the filesystem.
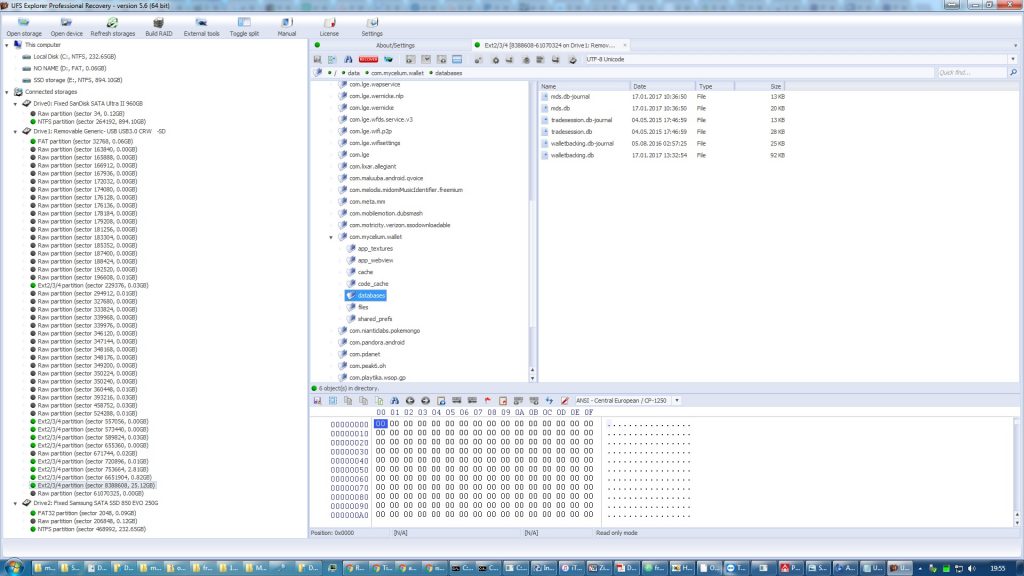
Android apps typically store data in the /data/com.myApp location, not accessible to the user unless they have root access. Within the app’s storage there is a databases folder that contains some SQLite databases with the data the app stores. Here I have gotten access to the Android filesystem using UFS Explorer and located the com.Mycelium.wallet folder and the databases within it.

The tricky part will be getting the data from the app’s database into something I can use, like a private key. I quickly opened up the databases in an SQLite database GUI but did not find anything that immediately indicated a private key of sorts. However, I decided that in the unlikely chance that Mycelium does not encrypt the private keys (more on this later), I could simply copy the database onto a working device and see if Mycelium would open it for me instead of having to parse through the database and search for the private keys manually.

Since the app’s folder and databases are hidden from normal users in the Android filesystem, I would have to get root access in order to copy the recovered databases over to the working phone. Luckily though there was a Moto G4 running Marshmallow at the shop, so unlocking the bootloader and rooting the device was about as simple and straightforward as it could get.

One swipe later and I was officially a super user! I copied over the recovered database folder to a microSD and put it into the phone.

And then downloaded Mycelium wallet and Solid Explorer from the Play store. Once they were installed I created a new wallet in Mycelium and then navigated to the /data/com.Mycelium.wallet folder in Solid Explorer.
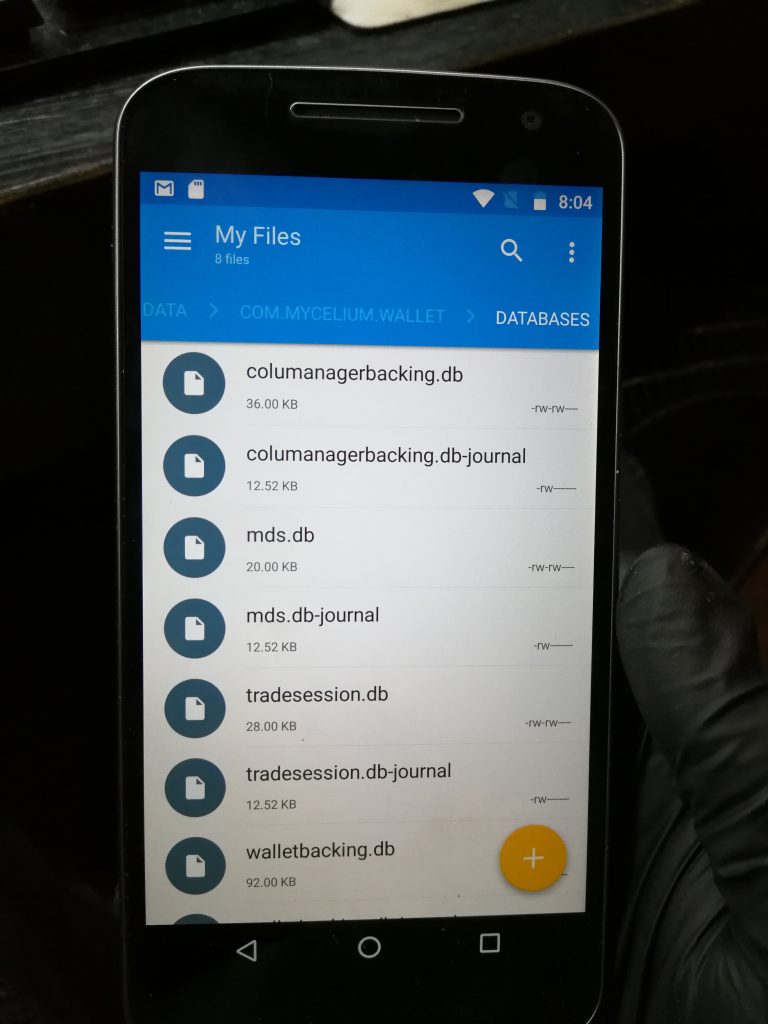
Then the recovered databases can be pasted into the folder. Now, will Mycelium open them?

YES! The wallet has been recovered! I now have full access to the private keys and can transfer them to cold storage or another wallet. That .5157 BTC wasn’t worth more than a few hundred dollars when the LG G3 was first released in 2014, but it certainly makes for a worthy recovery job today!
For better or for worse, I suspect the main reason why I was able to recover the wallet relatively easily once I had access to the old filesystem was due to: a) That Mycelium does not encrypt the private keys even when a PIN is set, or b) The decryption keys are stored with the private keys.
While it is less of a problem now that Android encypts the filesystem by default since Nougat, if a root exploit was to be released today then it would be extremely easy to extract the database from a victim’s device and copy it over to an attacker’s device, even with a PIN set in the app. Therefore I would caution all Mycelium wallet users to keep their devices up to date with security patches and don’t root them either.
BTC donations: 14YEMTwwbp1ELHqrxgRzt6uV1cE8pQZoFq
ETH donations: 0xb3de582ac74d3b08f1b667b165e71cbc0290f415
LTC donations: LcVoYM2EdbTCVNmMaBrSQBstZdkPVudaWr
XMR donations: 45StJrEa47G2UAXJi2DsvJMzMy9QZsjD89RKFZfWNuY2CaFWog4ixnwBBkxZKJVLcqggsyd1euYW56wV4QXn8zWRSbJVBFV
